Okta SCIM Set Up for User Provisioning, User Profile Data Mapping, and Group Member Management 👥
Before you enable user provisioning, it's a good idea to check your workspace notification settings. Once you turn on SCIM, users will receive notifications even if they haven't signed into their account yet! You can adjust your notification settings in the Admin Console on the Security Settings page.
Enable SCIM Provisioning
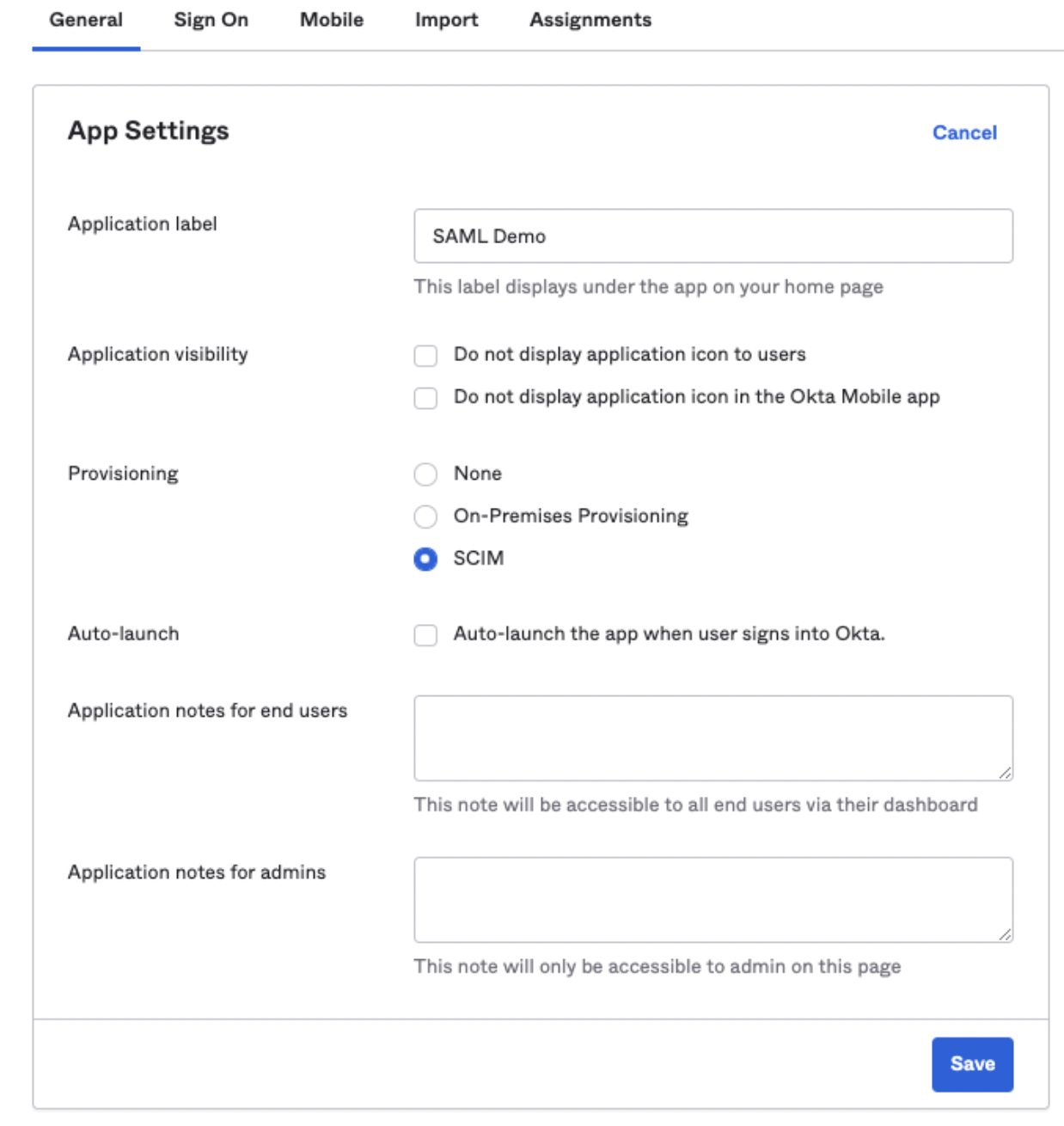
First, you'll need to enable SCIM provisioning within your Okta SAML application. Look for the setting to turn it on.
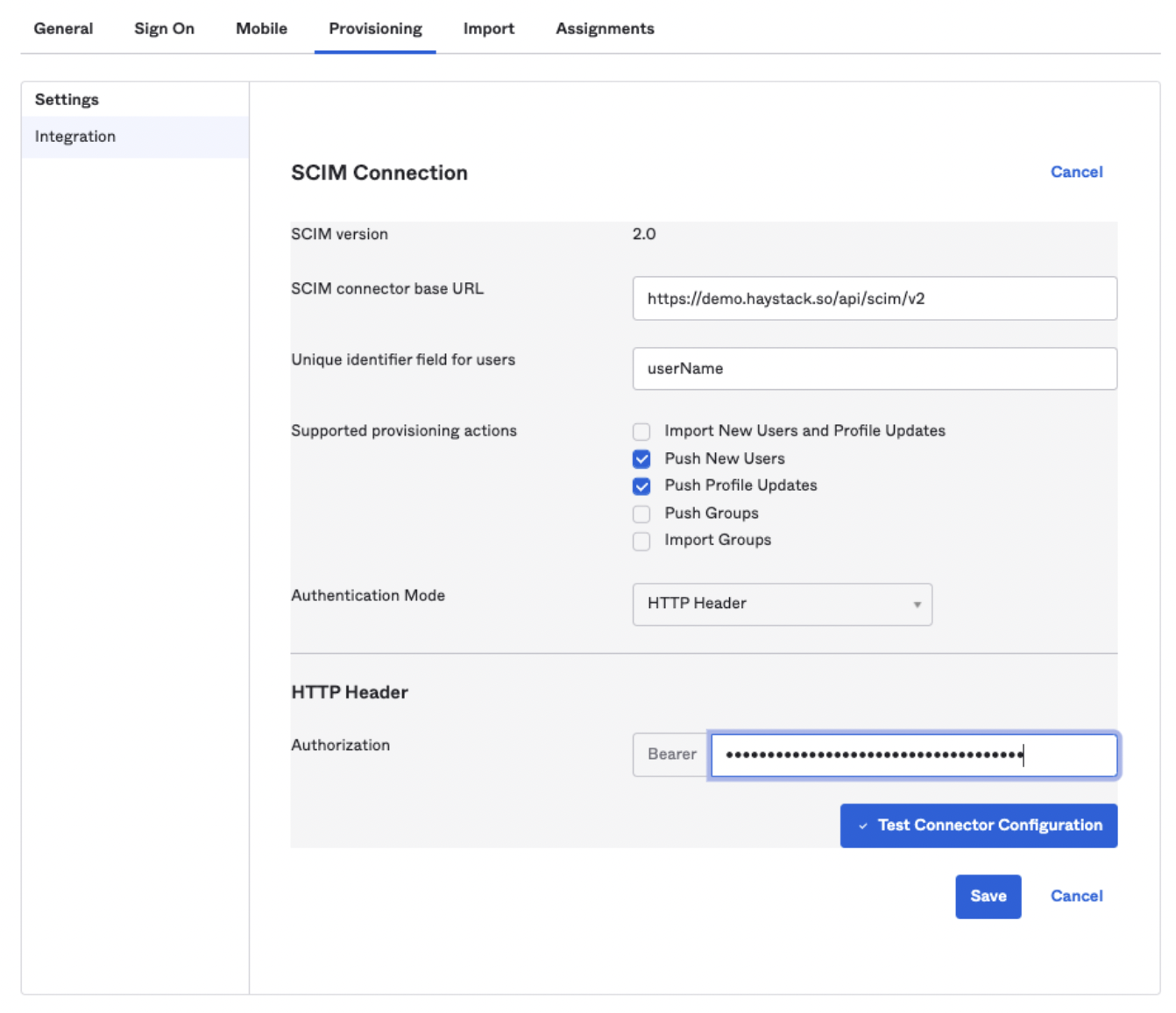
Next, you’ll configure the SCIM connection in the Provisioning tab. You'll need to enter the SCIM connector base URL and then click "Test Connector Configuration" to make sure it's working properly.
Remember: Be sure to replace the word "demo" in the URL with your unique Haystack subdomain.
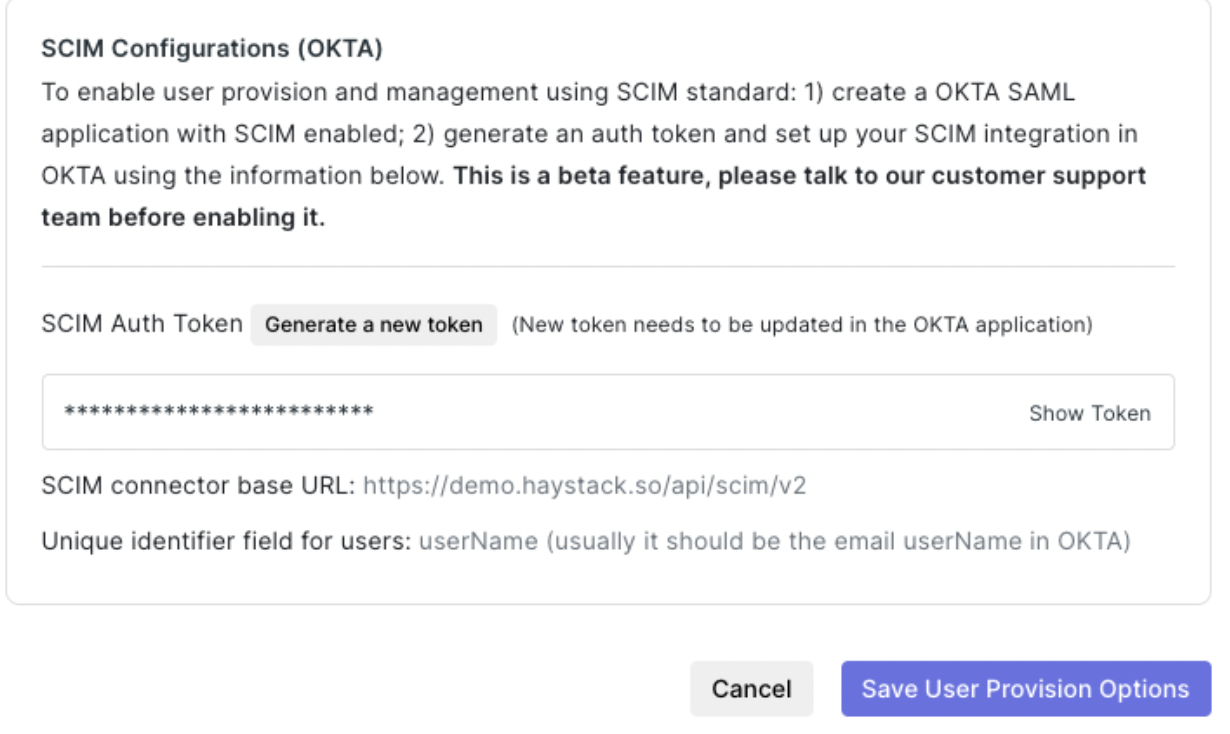
Copy the Bearer Token
Now, you'll need a special code to connect everything. Go to the User Provisions & Login section in your Haystack Admin Console and copy the Bearer token.
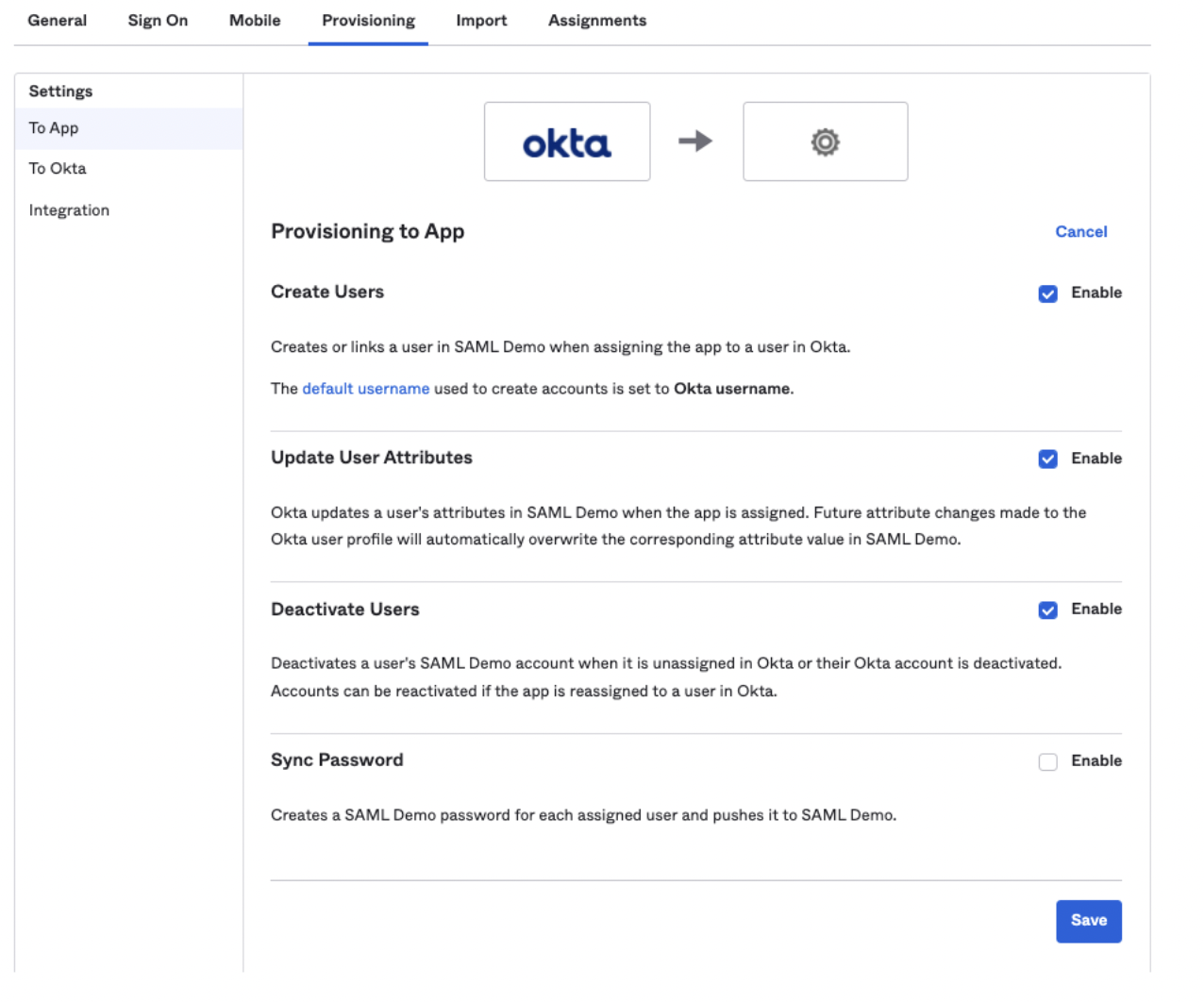
Configure "To App" Settings
Once the SCIM integration is saved, a "To App" tab will appear. Here, you'll choose what user attributes to send to Haystack. We recommend checking the following boxes:
-
Create Users
-
Update User Attributes
-
Deactivate Users
This ensures that users are automatically created, updated, and deactivated in Haystack as their status changes in Okta. Don't forget to save these settings.
Check for User Provisioning Errors
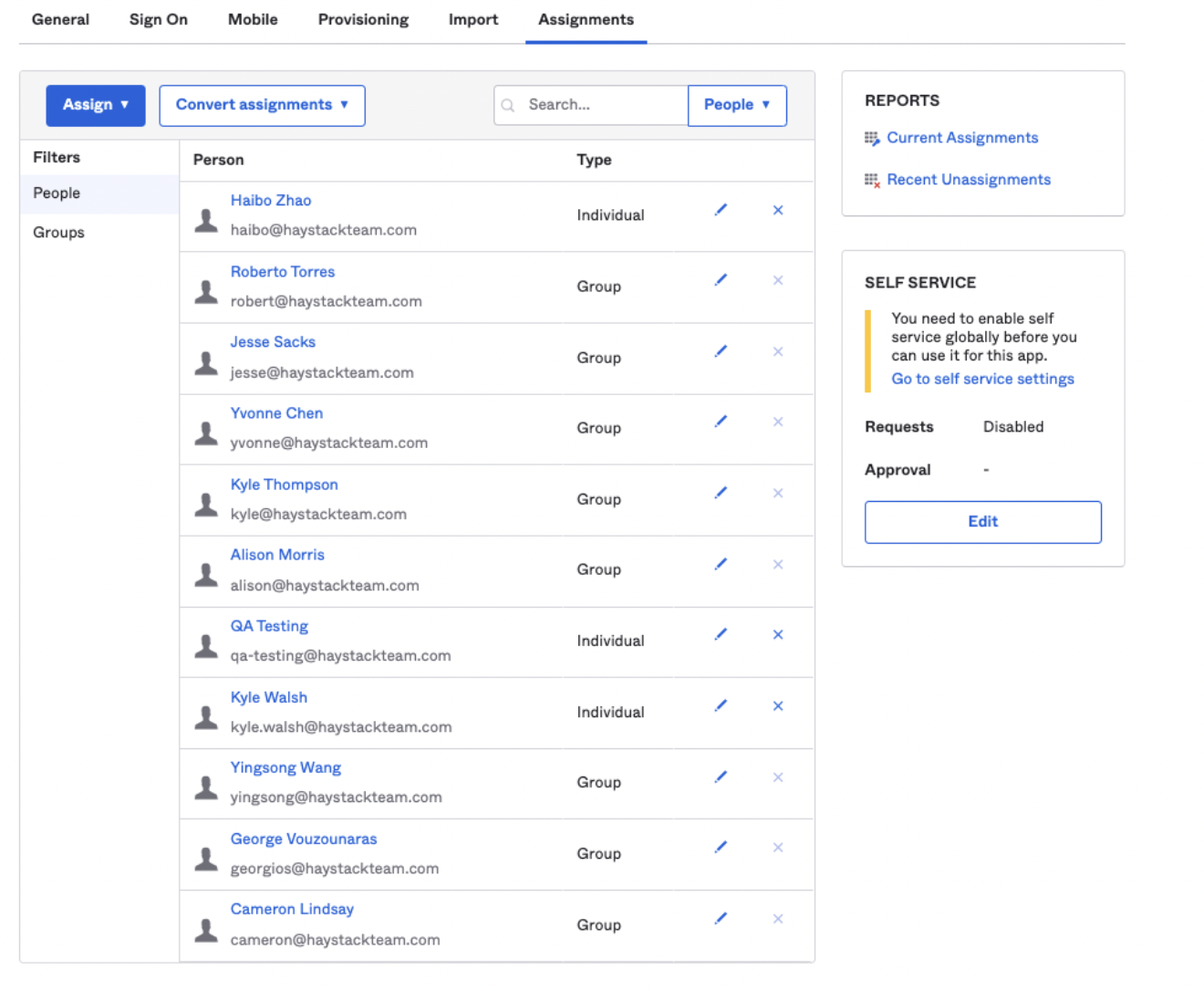
Now, head over to the Assignments tab to make sure everything is working correctly. Users and groups you've assigned will be provisioned in Haystack, and those who are un-assigned will be deactivated.
Sync Manager Relationships
It's super important to sync manager relationships! This is what allows Haystack to show the correct reporting structure on user profiles and for the org chart feature to work properly.
Make sure the “ManagerValue” field uses the Okta user ID (usually their email) of the manager. You can configure this in the Profile Editor by clicking "Go to Profile Editor" under the Provisioning tab, then choosing the profile mapping from Okta User to the SAML app.

Sync Custom Profile Fields
Haystack also supports syncing custom fields like "joinDate" and "photoUrl." Here's how to set that up:
-
Make sure the source field exists in your Okta user profiles.
-
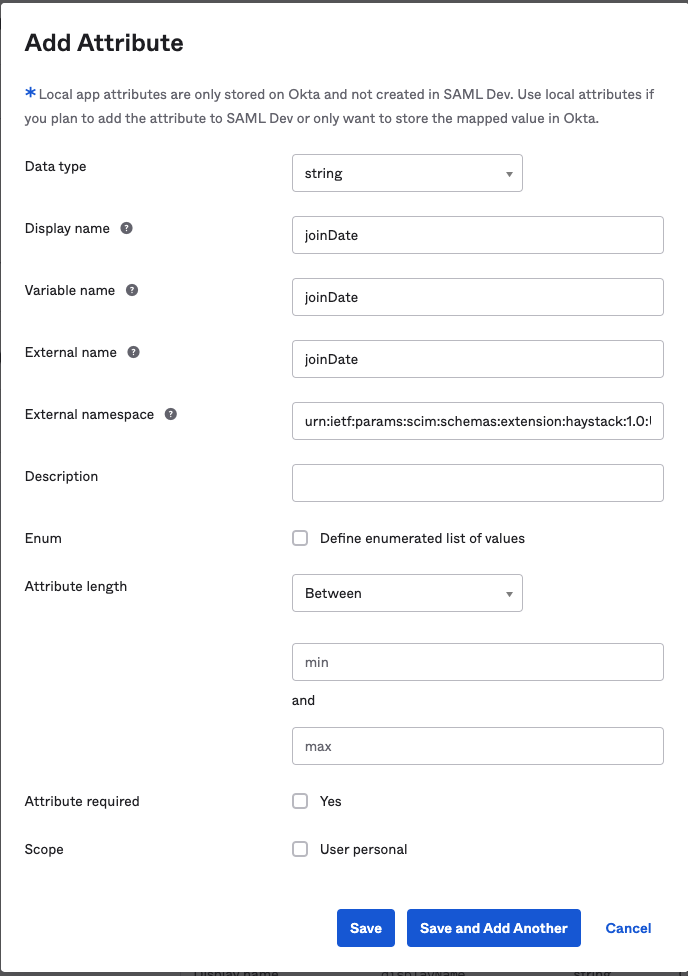
Add a new custom profile field in the Okta application for Haystack. Go to "Provisioning" -> "To App" -> "Go to Profile Editor" -> "+ Add Attribute." Be sure to use "urn:ietf:params:scim:schemas:extension:haystack:1.0:User" as the external namespace.
3. Add the new field to the mappings from the Okta profile. Make sure to apply it for both "Create and Update".

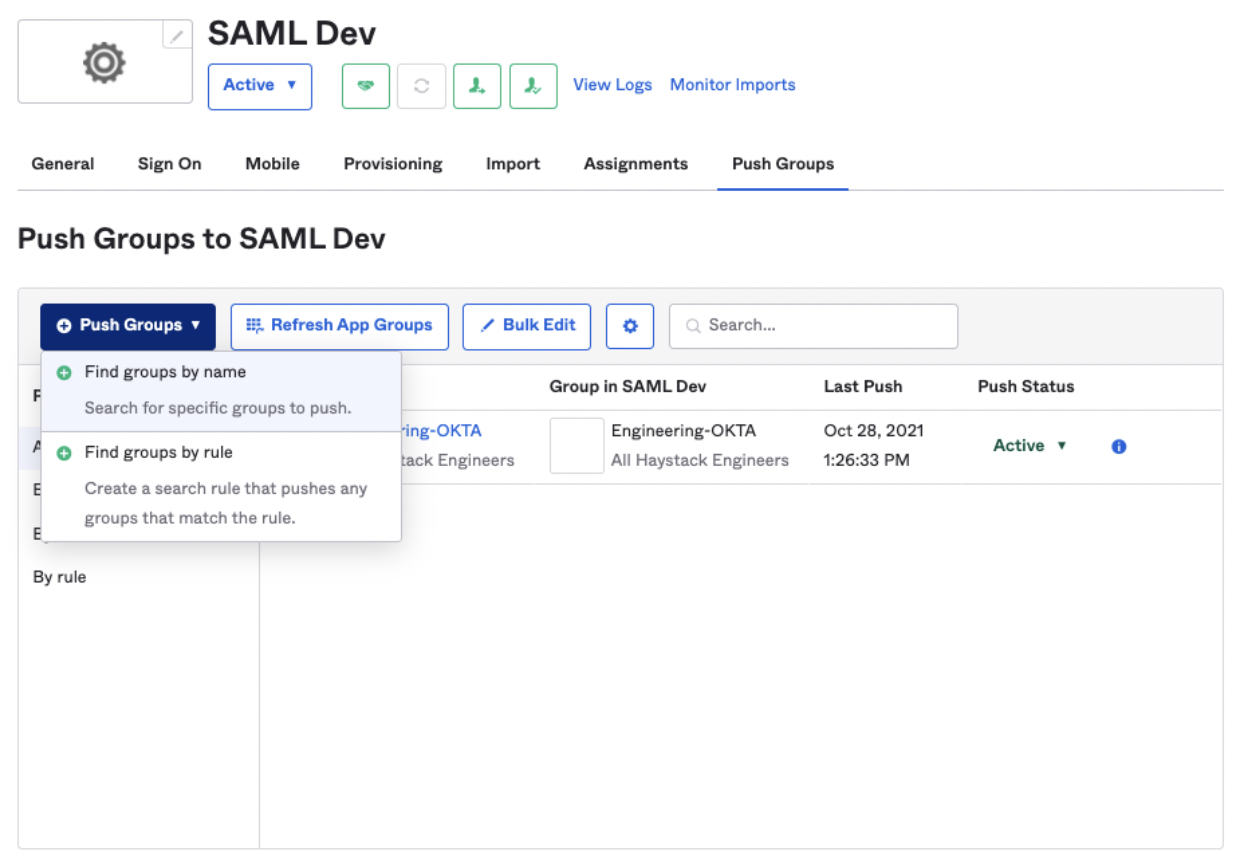
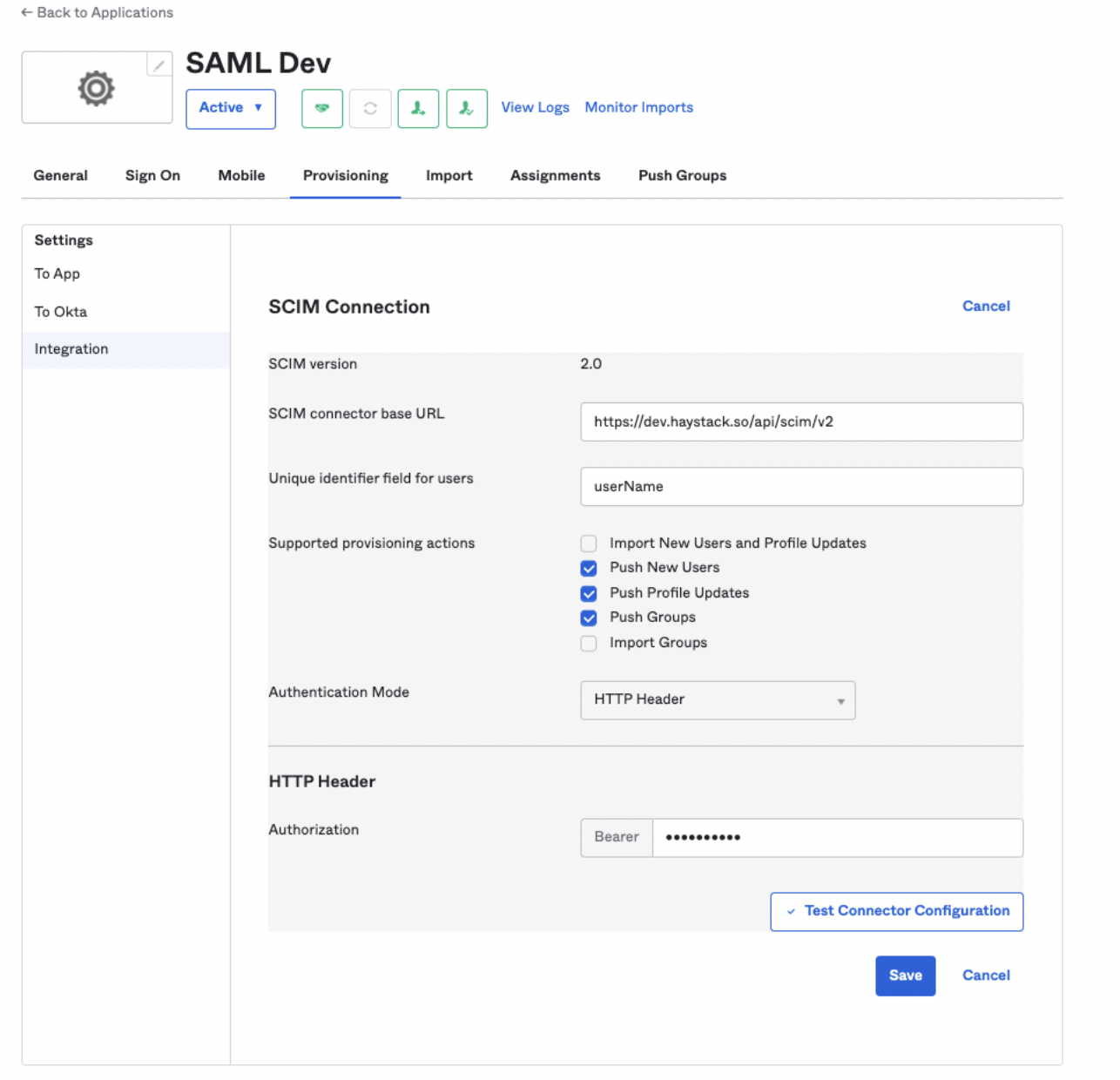
Sync Okta Groups to Haystack
Last but not least, you can also sync your Okta groups to Haystack.
-
Check the “Push Groups” box in the "Integration" settings under the "Provisioning" tab. You can also use "Test Connector Configuration" to make sure it's working.
2. Under the "Push Groups" tab, select the groups you want to push from Okta to Haystack.
You're all set! Your Okta integration is now configured for user and group provisioning.
Keywords: Okta, SCIM, user provisioning, user profile, group management, sync, security, guide, admin, provisioning, integration